Managing WMI Security
Microsoft has continually tightened up security access to the Windows Management Instrumentation (WMI) namespace. This is, in particular, as it relates to remote access. As most customers have their Job Schedulers on separate machines, the ability to receive events (as in the case of the AbatConsole which uses WMI for automatic refresh) can be impacted if proper security has not been set.
To maintain WMI security, the WMI Control MMC snap-in is used. This can be accessed via the Control Panel/Administrative Tools/Computer Management applet.
Also available via the Start Menu:
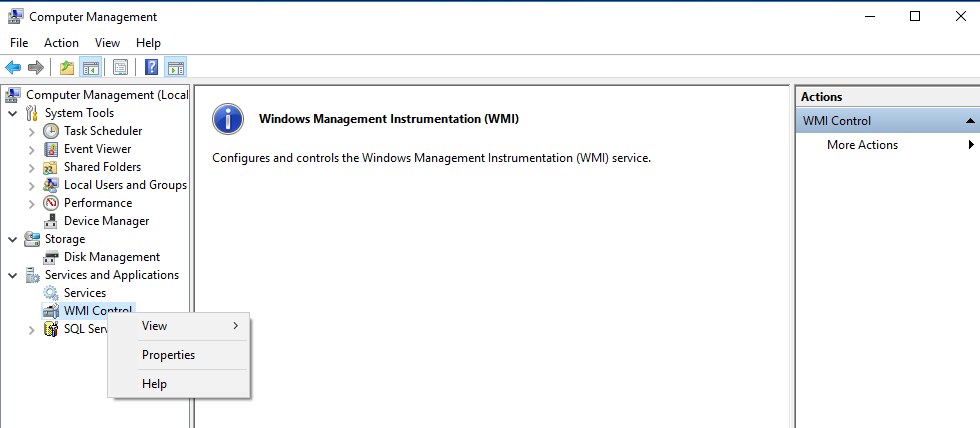
To execute WMI Control, right-click on the item and click “Properties”. A multi-tabbed dialog will appear. Look for the tab labeled “Security”.
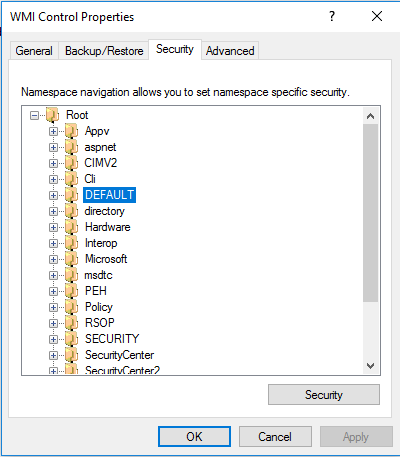
The WMI namespace will be displayed. Root\cimv2 is typically the namespace for most Win32 objects. ActiveBatch objects can be found in root\default (the item selected above). Click on the Security button and a dialog similar to this will be displayed.
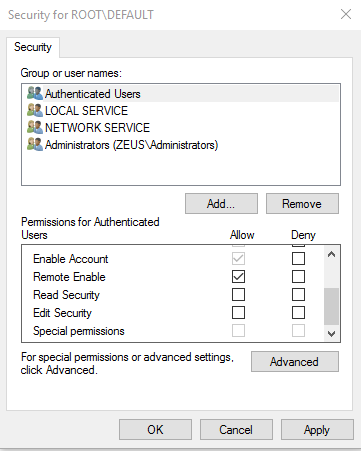
The Administrators group is granted complete access. The Everyone group is granted read level access but only on the local machine. Redwood Software recommends that you add the Authenticated Users group to this namespace and allow “Remote Enabled”.
Note: See the Troubleshooting WMI Knowledgebase article at the Redwood website if you experience any WMI-related issues.