Multi-Factor Authentication
Multi-Factor Authentication for ActiveBatch is supported in the ActiveBatch Console, Web Console, SSP, and Mobile Ops products and components. Introduced in V12 SP1, ActiveBatch currently supports MFA. Using any MFA authenticator app on your mobile / secondary device (such as Microsoft Authenticator, Google, Duo, etc), you can add a second factor of authentication (first factor being the traditional username/password) for when you log into an ActiveBatch Job Scheduler from any of the aforementioned clients.
Overview
You must be an ActiveBatch Administrator to perform MFA operations. When MFA is enabled on a Job Scheduler, users on their initial login to that Job Scheduler, will be required to setup MFA.
Once users are setup to use MFA, every time they log into the Job Scheduler, they will be required to provide a unique 6-digit code that only they have access to via the Authenticator app they initially used to setup ActiveBatch MFA. This code is prompted for after the user logs in with a valid username password, as a second step in the login process. Once a valid 6-digit code is entered, the user successfully logs in.
ActiveBatch uses the TOTP (Time-Based One Time Password) algorithm for generating and validating codes. TOTP is the industry recommended way of securing applications with 2FA (as opposed to SMS based 2FA, which has a long list of security issues).
MFA Settings
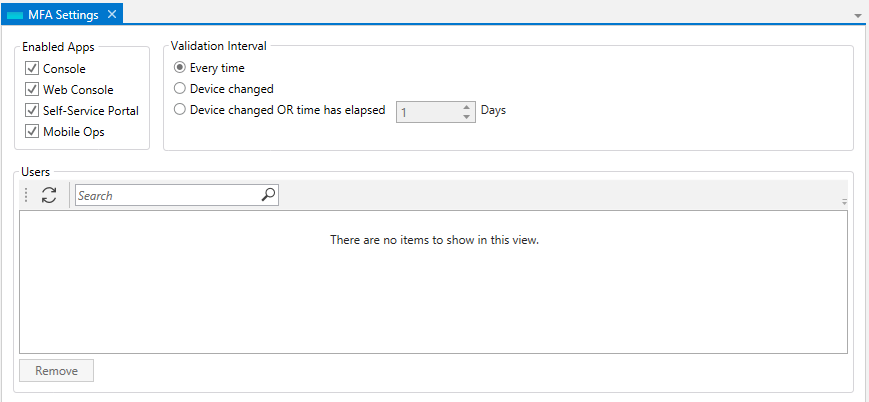
The dialog above controls MFA settings for the various component and product add-ins. The figure above has them all enabled for MFA. The Validation Interval controls how often the MFA should occur. The most conservative (and default) setting is “Every Time”. A more liberal setting is only when the device you’re using for ActiveBatch access has changed. This means MFA will occur only once. The last setting is to cause MFA to be performed when the Device has Changed OR when a specific number of days has elapsed.
Initial MFA Processing
When a user first logs in to an MFA enabled Job Scheduler, they will be presented with a series of dialogs if the initial username/password authentication is successful.
The first dialog presents a QR code which the user may scan on their phone with an acceptable MFA app of choice – and then their account will be added to the Authenticator app, and the app will generate unique 6-digit OTP codes on a 30 second time interval. Optionally, a user can enter in the secret key directly into the authenticator app instead of scanning the QR code by clicking on the blue eye.
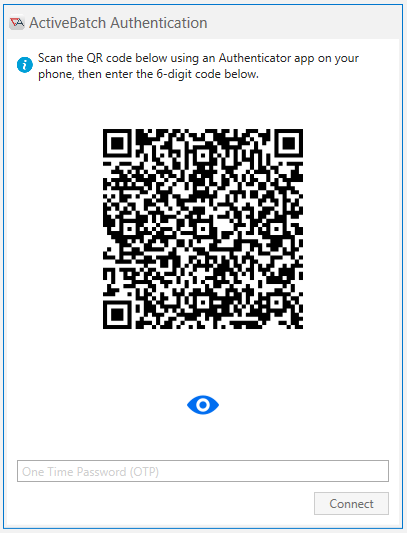
The user will then be asked to enter in the OTP code to validate that they have successfully added their account to their MFA app.
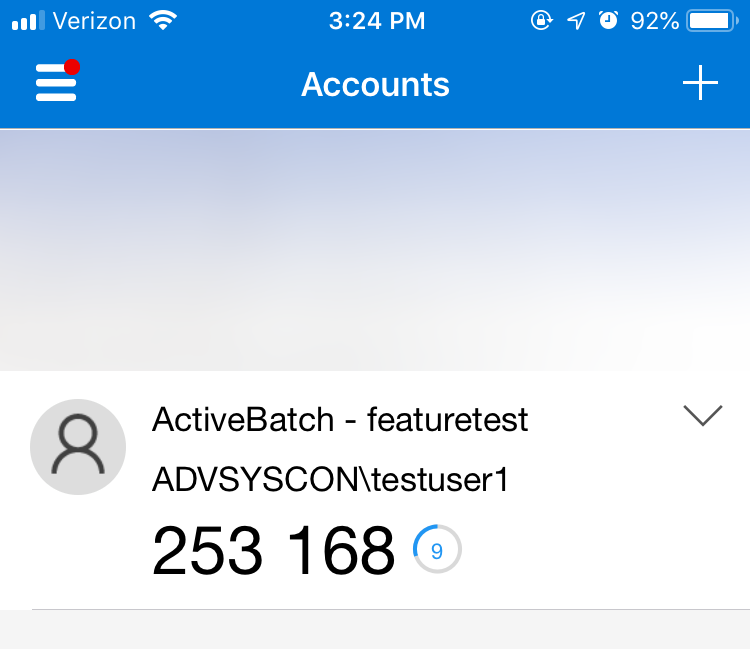
Once a valid TOTP code is entered, success will be indicated to the user, and they will subsequently be logged into the Job Scheduler.
Removing an MFA User
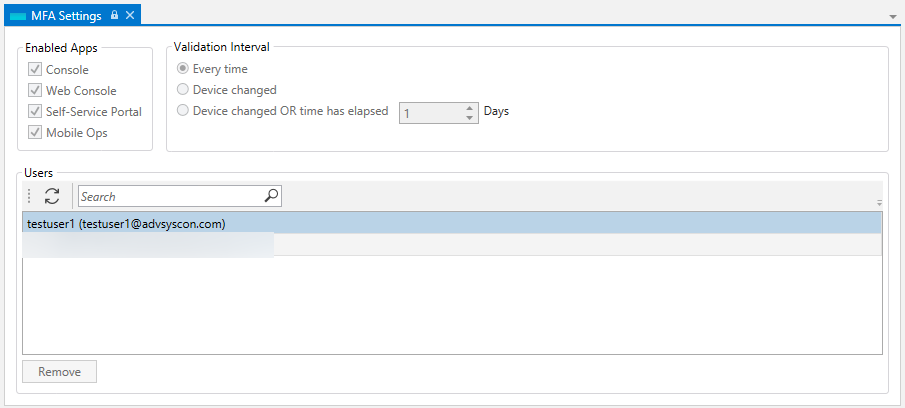
To remove a user who has been authenticated via MFA. Simple select the user to remove and click the Remove button. A confirmation message will appear. Click Yes if you’re certain you want to remove the user from the MFA list. Once you remove the user, s/he will have to fully authenticate again.